
Systems Architecture
7th Edition
ISBN: 9781305080195
Author: Stephen D. Burd
Publisher: Cengage Learning
expand_more
expand_more
format_list_bulleted
Question
1. Create a function named time() so that it displays elapsed time since startBtn is clicked in MM:SS format
2. Write html code that displays designer and time like the picture provided (on the side of an another div which contains table)
html:
<div>
<h3id="name">ROUTE DESIGNER: </h3>
<h3id="times">TIME: </h3>
</div>
<div id="anotherDiv" </div>
JS:
startBtn.addEventListener('click', startGame)
function startGame(){
document.querySelector('#name').innerHTML="ROUTE DESIGNER: "+nameInput.value
document.querySelector('#times').innerHTML="TIME ELAPSED: " + time
}
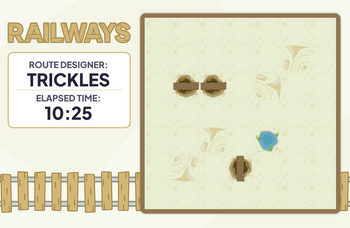
Transcribed Image Text:RAILWAYS
ROUTE DESIGNER:
TRICKLES
ELAPSED TIME:
10:25
SAVE
AI-Generated Solution
info
AI-generated content may present inaccurate or offensive content that does not represent bartleby’s views.
Unlock instant AI solutions
Tap the button
to generate a solution
to generate a solution
Click the button to generate
a solution
a solution
Knowledge Booster
Similar questions
- Bob uses the RSA cryptosystem to allow people to send him encrypted messages. He selects the parameters: p=3,q=17,e=3,d=11arrow_forwardOld MathJax webview provide answer as soon as possiblearrow_forwardWrite ARM Assembly program to do: - ISBN Checksum Validator Use Keil uvision software to write and simulate an ARM assembly program that checks the validity of a given ISBN by verifying the checksum Helping Information to solve program : 1. An ISBN consists of nine digits plus a validation digit. 2. The digits are numbered from right to left as d1, d2 .. d10, with d1 being the validation digit. 3. You can define the ISBN number in a 10-byte array in the memory. Each digit is stored in a byte. 4. To check whether the ISBN is valid or not, the following calculations are performed: Result = (10 x d10 + 9 x d9 + ... + ix di + ... + 2 x d2) % 11 Calculate d1 11 - Result If the calculated d1 equal to the d1 in the input ISBN then it is valid If d1 = 10, it is written 'X' For example, given the following ISBN: ISBN = 5123487654 ISBN= 5 1 2 3 487654 d10 d9 d8 d7 d6 d5 d4 d3 d2 d1 Result = x 10 + x 9 + x 8 + x 7 + x 6 + x 5 + x 4 + x 3 + x 2 mod 11 = 216 mod 11 =7 d1 = 11 - Result = 11 -7 =4 ,…arrow_forward
- CS 386 Project: Overview Project Synopsis: This group project will require your group to design and implement your own enciphering algorithm. Your team's algorithm must combine the two operations, substitution and permutation/transposition, into your unique encryption algorithm. Your encryption algorithm must include multiple rounds of the two operations. You program must be able to encrypt and decrypt messages. Your team will need to give your algorithm a name that is unique to your encryption technique. Your group mayarrow_forwardThe owner of KFC wants to use a system to record the orders for the hamburgers. KFC accept the orders via phone calls. When registered customers call KFC on the phone, they are asked their phone number. If the customer is not a registered customer, then a new record is created for the customer. When the phone number is typed into a computer, the name, the email address and the address of customer are automatically brought up on the screen. After taking the order, the total, including tax is calculated. Then the order is given to the cook. A receipt is printed. Sometimes, discount coupons are printed so the customer can get a discount. Carriers who make deliveries give customers a copy of the receipt and a coupon (if there is any). Weekly totals are kept for comparison with last month’s performance. 1.Write a summary of business activities for taking an order.. 2. Draw a context-level data flow diagram.. 3. Draw a level-0 data flow diagram..arrow_forwardCould you give me an example of how the line-waiting procedure works?arrow_forward
- TCP MULTIPLEXING AND DEMULTIPLEXING In the scenario below, the left and right TCP clients communicate with a TCP server using TCP sockets. The Python code used to create a single welcoming socket in the server is shown in the figure (the welcoming socket itself is not shown graphically); code is also shown for the client sockets as well. The three sockets shown in server were created as a result of the server accepting connection requests on this welcoming socket from the two clients (one connection from the client on the left, and two connections from the client on the right). mySocket = socket (AF_INET, SOCK_STREAM) mySocket.bind (myaddr, 6189 ); P1 Answer mySocket = socket (AF_INET, SOCK_STREAM) mySocket.bind (myaddr, 5854 ); ♫ transport QUESTION 1 OF 8 network link physical What is the source port # for packet C? www B source port: ? dest port: ? P4 HIGH A source port: ? dest port: ? P5 P6 transport network lirk physical mySocket1 = socket (AF_INET, SOCK_STREAM) mySocket1.bind…arrow_forwardTCP MULTIPLEXING AND DEMULTIPLEXING In the scenario below, the left and right TCP clients communicate with a TCP server using TCP sockets. The Python code used to create a single welcoming socket in the server is shown in the figure (the welcoming socket itself is not shown graphically); code is also shown for the client sockets as well. The three sockets shown in server were created as a result of the server accepting connection requests on this welcoming socket from the two clients (one connection from the client on the left, and two connections from the client on the right). mySocket = socket (AF_INET, SOCK_STREAM) mySocket.bind (myaddr, 6189 ); P1 mySocket = socket (AF_INET, SOCK_STREAM) mySocket.bind (myaddr, 5854 ); U transport network link physical QUESTION 2 OF 8 B source port: ? dest port: ? What is the destination port # for packet C? P4 P5 P6 transport network link physical A source port: ? dest port: ? mySocket1 = socket (AF_INET, SOCK_STREAM) mySocket1.bind (myaddr, 5262…arrow_forwardWrite a program in python language to get the copyright information and write copyright information code. I needed code with outputarrow_forward
- Cryptography is the study of protecting information. A cipher is a pair of algorithms ―the first algorithm encrypts a message and the second algorithm decrypts the message. In most cases, a unique key is also required to encode or decode plaintext. The Caesar cipher is one of the simplest and most widely known ciphers. It is named after Julius Caesar who allegedly used it to protect important military directives. Every letter in the plaintext is replaced by a letter N positions down the alphabet. For example, if N = 3, then a => d and b => e. While the idea is remarkably simple, it appeared to work in Ancient Rome. Most people there couldn't read, and those who could simply assumed it was a foreign language. Write a program that implements the Caesar cipher. You program will get from standard input the key N, followed by a line of plaintext. . . The key N should be any integer between 0 and 26 inclusive. If this isn't the case, print an error message and quit. Any numbers or…arrow_forwardcryptologyarrow_forwardHow many paths between E and F, no backtracking allowed.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Systems ArchitectureComputer ScienceISBN:9781305080195Author:Stephen D. BurdPublisher:Cengage Learning
Systems ArchitectureComputer ScienceISBN:9781305080195Author:Stephen D. BurdPublisher:Cengage Learning LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.Computer ScienceISBN:9781337569798Author:ECKERTPublisher:CENGAGE LNp Ms Office 365/Excel 2016 I NtermedComputer ScienceISBN:9781337508841Author:CareyPublisher:Cengage
LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.Computer ScienceISBN:9781337569798Author:ECKERTPublisher:CENGAGE LNp Ms Office 365/Excel 2016 I NtermedComputer ScienceISBN:9781337508841Author:CareyPublisher:Cengage

Systems Architecture
Computer Science
ISBN:9781305080195
Author:Stephen D. Burd
Publisher:Cengage Learning

LINUX+ AND LPIC-1 GDE.TO LINUX CERTIF.
Computer Science
ISBN:9781337569798
Author:ECKERT
Publisher:CENGAGE L

Np Ms Office 365/Excel 2016 I Ntermed
Computer Science
ISBN:9781337508841
Author:Carey
Publisher:Cengage