
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
Transcribed Image Text:Question 6
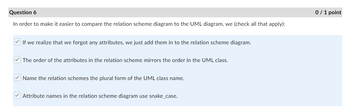
In order to make it easier to compare the relation scheme diagram to the UML diagram, we (check all that apply):
If we realize that we forgot any attributes, we just add them in to the relation scheme diagram.
The order of the attributes in the relation scheme mirrors the order in the UML class.
Name the relation schemes the plural form of the UML class name.
Attribute names in the relation scheme diagram use snake_case.
0 / 1 point
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Suppose you are going to design an instant messaging application called Telegraph. Telegraph is a modularized application composed of UI module, Chat module, and Contact module. The UI module uses the Chat module and the Contact module to render the user interface. The Chat module deals with sending and receiving messages. The Chat module uses the Network module for network communication. When users send/receive messages via the network, the Chat module uses the Crypto module to encrypt/decrypt the message. The Contact module manages the contact list. It also uses the Crypto module for encryption/decryption. The Crypto module uses the Math module for calculation. Now we propose a metric to measure the stability of modules. Formally, we define the "stability" of a module i as Si = a+dut where di" (i.e., incoming connection or dependency) is the number of modules that directly or indirectly USES module i and d?ut (i.e., outgoing connection or dependency) is the number of modules that…arrow_forwardWhat does it mean to be related? How do you define a relation's properties?arrow_forwardWhat precisely does "Identifier attribute" imply when it is used?arrow_forward
- Attributes from the identifying entity set's main key may be added to a weak entity set to make it strong. Please describe the overlap that will develop as a result of our choice.arrow_forwardQUESTION 3 A functor is a function symbol that names the relationship, but the name can be anything as long as it's a valid identifier. True Falsearrow_forwardRelationships in a use case diagram are a powerful mechanism to organize and reuse requirements. There are three main types of relationships in use case diagrams:1.Actor to actor—This is the generalization relationship and represented by the inheritance arrow in Figure 6.1. This relationship was also discussed in the previous chapter (notably Figure 5.3).2.Actor to use case—The relationship between an actor and a use case is called an association, also occasionally called "communication" because it represents a communication between the actor and the system. This association is represented by a straight line in Figure 6.1. The association is an interface through which an actor interacts with the system. Occasionally, an association line may have an arrowhead (not shown in Figure 6.1), representing the actor initiating the use case. This direction on the association relationship is only shown if absolutely necessary.3.Use case to use case—There are three specific relationships permitted…arrow_forward
- What is an example of a supertype/subtype connection in which the disjoint rule is applicable?arrow_forwardAn aggregation relationship in the domain model suggests the application of the Question options: creator pattern singleton pattern controller pattern expert patternarrow_forwardIn a class UML diagram, general relationships should be labelled with O cardinality O a relationship name direction of the relation all of the abovearrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education