
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
Please assist with this lab:
2.16 LAB: Port Scan (Modules)
In network security, it is important to understand port scanning. Hackers use tools to scan a network and determine if there are open ports and if they contain some sort of vulnerability. To scan ports, you first have to find active hosts on a network. Once you find active hosts and discover a list of IP addresses for those hosts, a port scan can be performed to gather information about open ports and analyze services running on those ports. A port scan is the process of sending packets to an active host's ports and learning details that can help you gain access to that host or to discover open vulnerabilities on your network.
Some common ports are:
Port 20 - File Transfer Protocol or FTP
Port 22 - Secure Shell protocol or SSH
Port 23 - Telnet protocol for unencrypted transfer
Port 80 - HyperText Transfer Protocol or HTTP
Port 443 - HyperText Transfer Protocol Secure or HTTPS
The Well Known Ports are those from 0 through 1023
We are going to simulate a port scan by filling a list with 100 random port numbers. These values will be used as the keys in a dictionary where the values will be randomly generated integers 0 / 1. The 0 will be a closed port and a 1 will be an open port.
Your first TODO is to create a function called "create_host_IPs( )" that randomly generates a list of 10 IP addresses with 4 random octets values, concatenating the 4 values into a string and appending it to a host list. The function returns the generated host list. The random values can be limited to a range of 10 to 200.
Ex: IPv4 address should look like this:
192.168.34.23
Your next TODO is to create another function called "simulate_scan(h)" that iterates through the host list (received as h ) and then creates a new list called open_ports. The function should use a nested for loop that iterates through the host list, and then iterates through the returned list from a call to "create_random_open_ports()". If the returned list value is 1, then append it to your open_ports list. This simulates a scan of all the IPs in the host list and creates randomly generated open ports. Finally it should print the host IP and a list of open ports as displayed in this example output.
Ex: Your output should contain 10 IP reports. Here is and example of 2 of the 10 reports:
Host IP: 66.78.126.11
Open ports are:
[53, 87, 21, 57, 71, 37, 61, 38, 45, 94, 84, 26, 72, 52, 75, 41, 90, 88, 82, 59, 50, 36, 60, 16, 51, 76, 24, 66, 33, 63, 86, 93, 34, 85]
Host IP: 11.96.129.20
Open ports are:
[15, 77, 19, 72, 78, 37, 93, 42, 26, 30, 79, 16, 47, 48, 43, 50, 82, 60, 46, 10, 62, 96, 12, 99, 76, 51, 32, 24, 61, 87, 73, 65, 85, 67, 29]
Current Code:
import random
def create_random_open_ports():
#Create empty list / dictionary
port = []
ports = {}
#Fill list with 100 random port numbers from 10 - 100
for i in range(1,101):
random_port = random.randint(10, 100)
port.append(random_port)
#Create a new dictionary with ports numbers as keys
new_ports = ports.fromkeys(port, 0)
#Iterate through new dictionary add random 0 / 1
#Closed port = 0, Open port = 1
for key in new_ports:
r1 = random.randint(0,1)
new_ports[key] = r1
return new_ports
# TODO: create a function called create_host_IPs() that randomly generates a list of 10 IP addresses
# concatenating the 4 values into a string and appending it to a host list. The function returns the generated
# host list
def create_host_IPs():
host = []
octet1 = ""
octet2 = ""
octet3 = ""
octet4 = ""
#Add loop with range 1 - 11 to create the 10 host IPs EX: 192.123.11.1
for i in range(1,11):
octet1 = str(random.randint(1,255));#Not taking 0 as first octet cannot
octet2 = str(random.randint(0,255));
octet3 = str(random.randint(0,255));
octet4 = str(random.randint(0,255));
host.append(octet1 + "." + octet2 + "." + octet3 + "." + octet4)
return host
# TODO: create a function called simulate_scan(h) that iterates through the host list (received as h ) and
# then creates a new list called open_ports. The function should use a nested for loop that iterates
# through the host list, and then iterates through the returned list from a call to create_random_open_ports().
# If the returned list value is 1, then append it to your open_ports list.
# This simulates a scan of all the IPs in the host list and creates randomly generated open ports.
# Finally it should print the host IP and a list of open ports as displayed in assignment information.
def simulate_scan(h):
open_ports = []
for i in range(len(h)):
random_ports = create_random_open_ports()
for j in random_ports:
if random_ports[j] == 1:
open_ports.append(j)
print("IP Address :" + h[i] + " Open Ports :" + str(open_ports))
if __name__ == "__main__":
#Simulate port scanning for open ports
active_hosts = create_host_IPs()
simulate_scan(active_hosts)
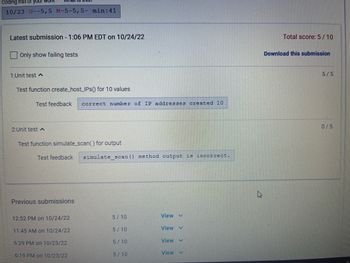
Transcribed Image Text:**Submission Details**
- **Latest Submission**: 1:06 PM EDT on 10/24/22
- **Total Score**: 5 / 10
- **Download Option Available**: Yes
**Unit Tests Overview**
1. **Test 1**
- **Function**: `create_host_IPs()` for 10 values
- **Result**: Passed
- **Score**: 5 / 5
- **Feedback**: Correct number of IP addresses created (10).
2. **Test 2**
- **Function**: `simulate_scan()` for output
- **Result**: Failed
- **Score**: 0 / 5
- **Feedback**: `simulate_scan()` method output is incorrect.
**Previous Submissions**
- **12:52 PM on 10/24/22**: Score 5 / 10
- **11:45 AM on 10/24/22**: Score 5 / 10
- **6:29 PM on 10/23/22**: Score 5 / 10
- **6:19 PM on 10/23/22**: Score 5 / 10
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps with 2 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Using a firewall, your computer is shielded from possible dangers on the internet. It's crucial to stick to certain standard procedures while dealing with packet filtering software.arrow_forwardThrough the use of a firewall, your computer is protected from any possible dangers that may originate from the outside world.When dealing with software that does packet filtering, it is important to follow a few best practices that have been established.arrow_forwardIn order to pre-configure the public key, a server administrator must utilize a specific SSH client file.arrow_forward
- Explain what two types of firewalls you have seen at the network layer.arrow_forwardThe use of a firewall helps to protect your computer from threats that might originate from the outside world.When dealing with packet filtering software, it is important to follow a few best practises that have been established for the programme.arrow_forwardThe installation of a firewall on a computer protects it from outside threats.A few guidelines must be observed when utilising packet filtering software.arrow_forward
- Explain the process of establishing a secure connection using the SSL/TLS protocol suite, including the role of certificates and key exchange.arrow_forwardPlease help with HW question(s) V Of the following steps that describe the development of a botnet, which best describes the step that comes first Spammer pays a hacker for use of a botnet. Controller server instructs infected systems to send spam to mail servers. Infected server sends attack commands to the botnet. Malicious code is sent out that has bot software as its payload.arrow_forwardBecause of the use of a firewall, your computer is guarded against dangers that may come from the outside world.When working with packet filtering software, it is absolutely necessary to adhere to a few standard operating procedures.arrow_forward
- Firewalls provide for the prevention of computer intrusions. A variety of distinct parameters are required by the software that filters packets.arrow_forwardYour computer is shielded from potential threats coming from the outside world via a firewall.When working with software that does packet filtering, there are a few guidelines that should be adhered to.arrow_forwardYour computer is protected from external attacks via a firewall.When using packet filtering software, there are a few rules to remember.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education