Question
a)The attackers are always looking for ways to obtain control of a computer connected to the
Internet. Brian Krebs, author of the popular information security blog, krebsonsecurity, has plotted the
possible uses of a compromised PC19 (Figure below).
Internet. Brian Krebs, author of the popular information security blog, krebsonsecurity, has plotted the
possible uses of a compromised PC19 (Figure below).
b)If your PC were compromised, provide a brief description of how your PC could be used by an
attacker to perform any three of the above activities. Be very specific and detailed in your answer
attacker to perform any three of the above activities. Be very specific and detailed in your answer
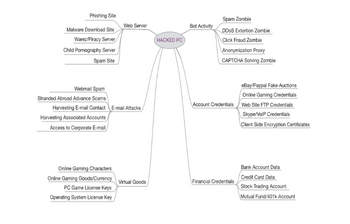
Transcribed Image Text:Phishing Site
Malware Download Site
Warez/Piracy Server
Child Pornography Server
Spam Site
Webmail Spam
Stranded Abroad Advance Scams
Harvesting E-mail Contact E-mail Attacks
Harvesting Associated Accounts
Access to Corporate E-mail
Web Server
Online Gaming Characters
Online Gaming Goods/Currency
PC Game License Keys
Operating System License Key
Virtual Goods
HACKED PC
Spam Zombie
Bot Activity DDOS Extortion Zombie
Click Fraud Zombie
Anonymization Proxy
CAPTCHA Solving Zombie
eBay/Paypal Fake Auctions
Online Gaming Credentials
Account Credentials Web Site FTP Credentials
Skype/VolP Credentials
Client Side Encryption Certificates
Financial Credentials
Bank Account Data
Credit Card Data
Stock Trading Account
Mutual Fund/401k Account
SAVE
AI-Generated Solution
info
AI-generated content may present inaccurate or offensive content that does not represent bartleby’s views.
Unlock instant AI solutions
Tap the button
to generate a solution
to generate a solution
Click the button to generate
a solution
a solution
Knowledge Booster
Similar questions
- Sam transmitted an information over the network to David. David noticed that the information was modified during the transmission. What type of security protection was breached? A. Confidentiality B. Authentication C. Integrity D. Availabilityarrow_forwardHi, I need to answer this question. The name of the book is "Computer Security and Penetration Testing, 2nd Edition". Thank you. Question: What is spoofing and how can it be used in an attack?arrow_forwardWhat kind of authorization, authentication, roles, and mitigation techniques are utilized in small, medium, and big hospitals to limit access? How may these four precautions lessen the possibility of becoming a ransomware target?arrow_forward
- Find three online security-related websites on the internet. Use whichever method you choose, and provide a succinct (2–3 paragraph) overview of each.arrow_forwardWhat is a possible vulnerability for each letter of the acronym STRIDE: spoofing, tampering, repudiation, information disclosure, denial of service, elevation of privileges.arrow_forwardI NEED URGENTLY, PLEASE Justify the use of a range of security techniques in typical situations. It may help to consider what would happen without the security mechanisms and go from there. A- is user’s permissions B-is Encryption C- is Anti-Virus D- is Firewallarrow_forward
- Authentication and Access Control are two distinct concepts. For each, describe and provide three examples of each (not including passwords) regularly used by companies. It is important to explain why NIST has revised its position on strong passwords. Are there any new recommendations from the NIST?arrow_forwardScoutSuite, Pacu, and Powler are all cloud security technologies. What are the distinctions between them? When it comes to verifying the integrity of the cloud environment and risk mitigation strategies, what technologies may be used?arrow_forwardWhat exactly is multifactor authentication and why is it useful? What role does it play in the protection of stolen passwords?arrow_forward
arrow_back_ios
arrow_forward_ios