
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Transcribed Image Text:البوابة التعليمية الإلكترونية لجامعة الإسراء
Ivy CouiUses
Course I|ITOINTIulivn
IVIIutenTI
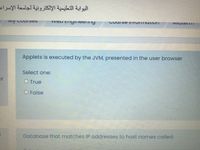
Applets is executed by the JVM, presented in the user browser
Select one:
of
O True
O False
Database that matches IP addresses to host names called:
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- You had previously prepared a file that you intended to use in a dictionary attack against a target server that didn't use salt. The 171,000 words in this file, excludingarrow_forwardBOB ALICE MD Нash Function message No Same? Yes discard Attacker Insecure Hash Function medium MD message Study the MD scheme that is shown in the scenario above, and answer the following question: This MD scenario doesn't solve the attack that is known as Man-in-the-middle attack with a false message. Explain how the MAC scheme if added into this scenario, can protect the communication from the so called Man-in-the-middle attack with false message.arrow_forwardHow does a server know that one of the far-off objects he gives his clients could be collected since it is no longer in use?arrow_forward
- What are a few benefits of utilizing a hash index table?arrow_forward7. Complete the following sentence: Templating is an example of ... O A POST request Separation of Concerns (SOC) A GET request HTTP request methods Incorrect Templating is unrelated to the HTTP methodarrow_forwardWhat are a few benefits of utilizing a hash index table?arrow_forward
- What advantages do File System websites have over HTTP websites? What makes encapsulation and inheritance different from one another?arrow_forwardWhat are a few benefits of utilizing a hash index table?arrow_forwardSocket programming The application consists of two parts: Server and Client. Each part can run independently on separate computers. Server manages the chat session. It maintains a list of the active clients and forwards incoming messages. The Server is multithreaded - communication with each client is through a separate thread. When Server is started, it starts to wait for client connections. This thread continues forever to listen for clients. When a connection request is received, the server starts a thread to service the client. This is necessary for each client to have its own socket. When the thread is started, a Client object is created containing all the relevant info about each client and saved in a list. The ServiceClient() thread is where all the work is done. ServiceClient() defines the implementation of the server side of the application protocolarrow_forward
- Digital forensics: Suppose that we a record but not sure which one is the original one and which one has been modified: A) Bob leaves the hotel at 7:00 pm B) Bob leaves the hotel at 6:00 pm Fortunately, we have the hash value of the original record, calculated by SHA-256: 2655a8151189efae706db96460d368ab6adb9f5a1b88e5aa5c6ea18ba65beadd Please tell us which one is the original one, A or B? (Hint: You can use the SHA-256 calculator at https://xorbin.com/tools/sha256-hash-calculator).arrow_forwardHashing is a process of converting input data of arbitrary size into a fixed-size output, typically a sequence of characters or digits that represents the original data. The output, known as a hash value or message digest, is generated using a mathematical function called a hash function. Hashing is commonly used in computer science and cryptography to ensure data integrity, security, and efficient data retrieval. It is a one-way function, meaning that it is easy to compute the hash value from the input data, but it is practically impossible to reconstruct the original data from the hash value. The topics of interest include hashing, hash tables, collision detection, temporal complexity, and hashing applications.arrow_forwardOTP Cipher is an example of stream Cipher. State TRUE OR FALSE Select one: True Falsearrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY