
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
I need the answer as soon as possible
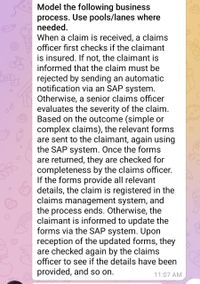
Transcribed Image Text:Model the following business
process. Use pools/lanes where
needed.
When a claim is received, a claims
officer first checks if the claimant
is insured. If not, the claimant is
informed that the claim must be
rejected by sending an automatic
notification via an SAP system.
Otherwise, a senior claims officer
evaluates the severity of the claim.
Based on the outcome (simple or
complex claims), the relevant forms
are sent to the claimant, again using
the SAP system. Once the forms
are returned, they are checked for
completeness by the claims officer.
If the forms provide all relevant
details, the claim is registered in the
claims management system, and
the process ends. Otherwise, the
claimant is informed to update the
forms via the SAP system. Upon
reception of the updated forms, they
are checked again by the claims
officer to see if the details have been
provided, and so on.
11:07 AM
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- How an RSA cryptosystem is different from a digital signature scheme? I need to submit within an hour. Please help me.arrow_forwardWhat's the difference between cryptography's private and public keys?arrow_forwardPlease tell me the names of the three most important operations in the field of cryptography.arrow_forward
- Why are prime numbers important in cryptography?arrow_forwardDo you know what you're trying to accomplish with this process? Decide on which types of authentication have which pros and drawbacks.arrow_forwardWhen it comes to cryptography, what is the difference between symmetric and asymmetric?arrow_forward
- What is it about authentication that causes so much worry in the modern world?arrow_forwardHow do I find my access code?arrow_forwardAre there any possibilities for the data and connections to be encrypted from start to finish? What are the advantages of doing this? I would appreciate it if you could give me an illustration of how and why encryption is useful.arrow_forward
- What am I doing wrong if I want to acquire my access code for this book? I was wondering if there was any way that you could either help me discover it or give me information on how to find it on my Yuzu account.arrow_forwardWhat is the absolute bare minimal number of keys required to utilize public key cryptography?arrow_forwardQuestion 9 Full explain this question and text typing work only thanksarrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education