Question
Lucca wants to prevent workstations on his network from attacking each other.If Lucca's corporate network looks like the network shown here, what technology should he select to prevent laptop A from being able to attack workstation B?
A..IDS
B..HIPS
C..HIDS
D..IPS
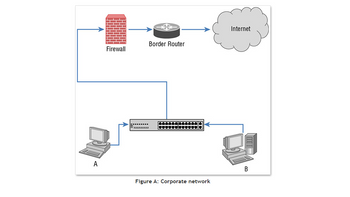
Transcribed Image Text:A
Firewall
‒‒‒‒‒‒‒‒‒
M
Border Router
Figure A: Corporate network
Internet
B
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps

Knowledge Booster
Similar questions
- Assess Network Security Threats and Vulnerabilities PC-PT PCO Server-PT Server StcPT Switch PC-PT PC1 Router-PT Router Router PT Router Sytch- Switch1 PC-PT PC3 PC-PT PC2 Examine the network diagram. 1. List potential threats and explain how they could impact the network. 2. Identify specific vulnerabilities within the current setup. Threats Vulnerabilities Implement Countermeasures for Identified Threats and Vulnerabilities Suggest practical measures to mitigate identified threats and vulnerabilities.arrow_forwardYour new SOHO router allows you to configure security settings as part of the setup process. How secure are your communications with each option?PSK, AES, WEP, TKIP, and RC4 are all examples of cryptographic protocols.arrow_forwardHello, I have to write a paper on the topic of network instrusion detection. I have some questions on how to get started with some sections of my paper. resources and or references is a plus! there's so much info out there! 1. how is IDS part of a larger defense in depth strategy? 2. who are some of the larger players in the space, both commercial and open source? 3. how would you implent and IDS on a network if you needed to? Any help, sites, sources are much appreciated!arrow_forward