
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Concept explainers
Question
thumb_up100%
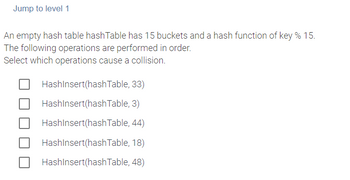
Transcribed Image Text:Jump to level 1
An empty hash table hashTable has 15 buckets and a hash function of key % 15.
The following operations are performed in order.
Select which operations cause a collision.
HashInsert(hashTable, 33)
HashInsert(hash Table, 3)
HashInsert(hash Table, 44)
HashInsert(hash Table, 18)
HashInsert(hash Table, 48)
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Java - Hash table valsTable is shown below. The hash function is key % 5.arrow_forwardA hash table with non-negative integer keys has a modulo hash function of key % 15. Hash function index range: 0 to Ex: 5 Item 110 will go in bucket Ex: 26arrow_forwardPassword Cracking Each student should be able to access* one PassXX.hash file. This file contains 4 unsalted md5 password hashes (md5 is commonly used for hashing passwords, though it is a bit weak for modern use. It is very important to salt passwords before hashing them, since leaving them unsalted makes them easier to crack. However, many sites fail to do this). Your assignment is to use Hashcat (or another password cracking or password "recovery" tool) to retrieve the original passwords from the hashes, and submit the password/hash pairs. Each set of hashes contains 1 very easy password and 3 slightly challenging passwords of differing format. Link to hashcat: https://hashcat.net/hashcat/ Note: You will also need one or more dictionaries to perform a dictionary attack. *access: Files are accessible based on your last name. You should see a large number of files that are not accessible due to your account having a wrong last name, and one file that is accessible that lacks…arrow_forward
- The following are applications of hash functions EXCEPT FOR Question 15 options: AES encryption algorithm Storing Passwords File synchronization Digital Signaturesarrow_forwardQuestion 23arrow_forwardUsing double Hashing, insert items with keys: 69, 86, 33, 47, 17, 55 into an empty hash table. tableSize: 7 hash1(x) = x mod tableSize. hash₂(x) = R-(x mod R), R is a prime number smaller than tableSize hash1(x) + hash2(x) mod tableSizearrow_forward
- The following hash table uses linear probing for collision resolution and the hash code value calculation simply returns the full integer value of the key. Based on the data in this table, list two possible different valid orders that the data could have been inserted into it. List the inserted value order with a space between each value and no commas. 0 42 1 14 2 21 3 4 5 19 6 Blank # 1 A Blank # 2 A/arrow_forwardQuestion twoarrow_forwardJump to level 1 Hash table valsTable is shown below. The hash function is key % 5. Assume items are inserted at the end of a bucket's list. valsTable: o 50 1 2 12 3 49 After the operations HashInsert(valsTable, item 100) item 26) HashInsert(valsTable, Select the bucket containing the following items: 26 Select 50 Select 0 100 1 2 2 3 5 3 4 Check Nextarrow_forward
- In a hash table of size 10, where is element 7 placed?a) 6b) 7c) 17d) 16arrow_forwardWhich of the following operations are done in a hash table?a) Insert onlyb) Search onlyc) Insert and searchd) Replacearrow_forwardvalsTable: o Empty-since-start 1 Empty-after-removal Occupied Hash table valsTable uses double probing with the hash functions hash1(key): key % 11 hash2(key): 5 - key % 5 and a table size of 11. 15 5 27 6. 7 HashInsert(valsTable, item 70) inserts item 70 into bucket Ex: 10 8 9 Hashlnsert(valsTable, item 62) inserts item 62 into bucket 10 Hashlnsert(valsTable, item 59) inserts item 59 into bucket 2. 3.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education