
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
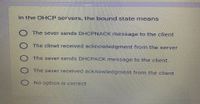
Transcribed Image Text:in the DHCP servers, the bound state means
The sever sends DHCPNACK message to the client
The clinet received acknowledgment from the server
The sever sends DHCPACK message to the client.
The sever received acknowledgment from the client
No option is correct
O0 00
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- In RPC (remote procedure call), while a server is processing the call, the client is blocked a. unless the client sends an asynchronous request to the server b. unless the call processing is complete c. for the complete duration of the connection d. none of the abovearrow_forwardQ1: Based on Kerberos protocol, find any mistakes if any, and then correct. S wants to communicate with B, when A is the trusted third party. S B:S, A B → S: (T, L, KAS, A}Ksp (Ts, L,KSa, S}«AR S A: (Ts,L, KAS, S}KAR (S, TA3KAS A S: (TA + 1}xAS 100% Give Feedback to Marrow_forwardAlgorithm to Auxiliary methods for the lockstep protocol.in: message m; set of recipients Rarrow_forward
- In IEEE 802.11, two-way communication is used to authenticate an open system. In order to authenticate the client, the server must give the station ID (typically the MAC address). Response to the client's previous request is either a successful or failed authentication response from the access point/router. An error may arise if, for example, an AP/router configuration does not include the client's MAC address.In what ways is it advantageous to use this kind of authentication scheme?In what ways does this authentication technique have security vulnerabilities that might be mitigated?arrow_forward1. A network has a DHCP server that manages a Class C network for IP addresses it gives out. Over the course of a week, 75- 80 people with devices come and go and their devices connect to the network each day. Often, by Wednesday or Thursday, people complain about not being able to connect to the network. Why can the lease life parameter be causing the problem?arrow_forwardQ5. DHKE protocol Use these toy parameters to demonstrate how DHKE (Diffie-Hellman Key Exchange) works: a large prime number p key a = 5, Bob's secret key b = 4. What are their public keys? How can they come up with an agreed session key at the end of the protocol and what is the agreed session key? = 13 and a generator g = 2, (p and g are in public domain), Alice's secret %3=arrow_forward
- Three-way handshake is used by a TCP client and a TCP server to establish a connection, as illustrated below: 1st: client:port1 -> server:port2, SYN 2nd: server:port2 -> client:port1, SYNACK 3rd: client:port1 -> server:port2, ACK When this client is performing scanning attacks, it will generated a large number of failed connections. In each failed connection, the three-way handshake fails to complete. People commonly use SYN together with the absence of its corresponding SYNACK in this same TCP session to identify whether this connection is failed. By investigating the failed connections, an engineer finds that in legitimate/benign cases, if the server does not return SYNACK to the client, the client will not send the ACK packet after SYNACK (e.g., the 3rd packet above). Therefore, this engineer suggests that we can count the failed connections based on the following rules without considering SYNACK:arrow_forwardDraw a sequence diagram for the following scenario. In a network, two nodes communicate with each other. These are the sequence. 1) Node J sends ping message to Node L 2) Node L sends ICMP echo reply to node L. Now Node A is having the MAC address of Node L. 3) Node J starts TCP handshake with Node L by sending SYN message. 4) Node L sends (SYN+ACK) back to node J. 5) Node J sends the ACK to Node L.arrow_forwardLet's say that Host C is running a Web server that listens on port 80. Suppose that this web server is able to maintain persistent connections and responds to requests from both Host A and Host B. Is Host C sending all of the requests over the same connection, or are there many sockets in use? Do each of them have port 80 even though they are broadcast over separate sockets? It's something you need to discuss and provide some clarification on.arrow_forward
- Three-way handshake is used by a TCP client and a TCP server to establish a connection, as illustrated below: 1st: client:port1 -> server:port2, SYN 2nd: server:port2 -> client:port1, SYNACK 3rd: client:port1 -> server:port2, ACK When this client is performing scanning attacks, it will generated a large number of failed connections. In each failed connection, the three-way handshake fails to complete. People commonly use SYN together with the absence of its corresponding SYNACK in this same TCP session to identify whether this connection is failed. By investigating the failed connections, an engineer finds that in legitimate/benign cases, if the server does not return SYNACK to the client, the client will not send the ACK packet after SYNACK (e.g., the 3rd packet above). Therefore, this engineer suggests that we can count the failed connections based on the following rules without considering SYNACK: If a client:port1 sends…arrow_forwardRule Direction In Out Out In Either ABCDE Src Addr Dest Addr Protocol Dest Port TCP TCP TCP TCP Any External Internal Internal External Any Internal External External Internal Any 80 >1023 80 >1023 Any Action Permit Permit Permit Permit Denyarrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education