
Understanding Business
12th Edition
ISBN: 9781259929434
Author: William Nickels
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
Q3- From the Learning Activity titled “Privacy Protection,” (please see the attached notes) identify two of the U.S. Federal Privacy Rights and Laws listed. Now, imagine you are a business analyst. What are some considerations you would make to ensure customer data is protected? In terms of creating a privacy policy, who would you involve in this process and why? If a manager asked you to provide him with a list of all customer emails for a marketing campaign, how would you respond? How would you determine if providing the list would be a violation of the company’s privacy policy?
Note- Privacy Protection is attached to view.
Transcribed Image Text:Privacy Protection
As you read this section on privacy rights in the U.S. and data protection laws in Europe,
consider the ethical and social issues that arise for businesses using information technology in
relation to employee and customer privacy. Share your thoughts about the ethical
implications of this practice in the Discussion Board. Be sure to respond to at least one other
post on this topic.
Privacy and freedom are important parts of every American's life, although many take these
rights for granted. Privacy is the right individuals have to be left alone, unobstructed, and free
from unwarranted interference or surveillance. When this right exists, it extends to all
individuals and protects them from other individuals, organizations, and government
agencies. Freedom refers to the absence of undue restriction or confinement and the
opportunity to exercise all inherent rights.
Privacy rights are protected in many countries, including the United States, Canada, and many
European nations. In the United States, the Bill of Rights within the Constitution protects not
only the right to privacy but also freedoms of speech, religion, and association. Table 2.1 lists
federal privacy rights and laws in the United States.
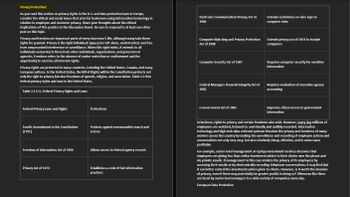
Table 2.1 U.S. Federal Privacy Rights and Laws
Federal Privacy Laws and Rights
Fourth Amendment to the Constitution
(1791)
Freedom of Information Act of 1966
Privacy Act of 1974
Protections
Protects against unreasonable search and
seizure
Allows access to federal agency records
Establishes a code of fair information
practices
Electronic Communication Privacy Act of
1986
Computer Matching and Privacy Protection
Act of 1988
Computer Security Act of 1987
Federal Managers Financial Integrity Act of
1982
E-Government Act of 2002
Extends restrictions on wire taps to
computer data
Extends privacy act of 1974 to include
computers
Requires computer security for sensitive
information
Requires evaluation of executive agency
accounting
Improves citizen access to government
information
In business, rights to privacy and certain freedoms also exist. However, every day millions of
employees are watched, listened to, and visually and audibly recorded. Information
technology and high-tech data retrieval systems threaten the privacy and freedoms of many
workers across the country by making the surveillance and recording of employee actions and
conversations not only very easy, but also relatively cheap, effective, and in some cases
profitable.
For example, senior-level management at Cyclops Investment Services discovers that
employees are giving less than stellar investment advice to their clients over the phone and
via private emails. If management in this case violates the privacy of its employees by
accessing their emails or by electronically recording telephone conversations, it may find that
it can better control the investment advice given to clients. However, is it worth the invasion
of privacy, even if there may potentially be greater profits in doing so? Dilemmas like these
are faced by senior level managers in a wide variety of companies every day.
European Data Protection

Transcribed Image Text:There is a much higher standard of rights of privacy of consumers in Europe than in the
United States. In Europe, businesses are not allowed to use the personal information of their
customers without prior consent. Such consent, referred to as informed consent, can only be
given when there is knowledge by the consent giver of all of the facts and information
required to make a rational decision. European countries also have tighter protection as to
what personal data may be transmitted across county borders and out of the European
Union. This has led to interesting court cases as Web servers within a country make data
available to the Internet without consideration that the data may be accessed from clients
(browsers) outside the borders. Court rulings have upheld that just because data
was available beyond borders does not mean that it was accessed beyond the borders,
therefore not in violation of privacy laws.
Although the United States does not have the same level of consumer protections in place,
U.S. companies must adhere to these stricter guidelines and provisions when doing business
with European companies or with European consumers. Although there may not be
government enforcement of such policies, safe harbor frameworks are in place. A safe
harbor is a self-regulating policy that, in absence of government regulation or enforcement,
acts to meet regulations set by governments. With safe harbor policies in place, European
and American joint business ventures thrive.
Technology integration provides opportunities to both serve organizations and their
customers. However, it also opens up the possibility of infringing on individuals' privacy and
freedom. Organizations that utilize voice over IP (VOIP) telephone service are able to provide
exception services beyond what a more traditional private branch exchange (PBX) system can
provide. When a customer calls into a VoIP system, the system is capable of looking up the
caller's phone number, looking up past communications (orders, problem resolution, and
anything else that the organization has stored), all before the call has been answered. As a
customer's call may be transferred, all data associated with the call is also transferred. This
may be great for customer service, but also reduces the privacy of the caller and the ability
for an anonymous inquiry is lost.
Next ActivityScroll To Top
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- How would you rate the quality of the results of an Internet search?arrow_forwardParaphrase this one. Against the backdrop of today's healthcare landscape, replete with the imperative to maximize resource efficiency, predictive analytics emerges as an indispensable tool. Its deployment empowers healthcare establishments to enhance both financial and operational decision-making, optimize the delicate balance of inventory and staffing levels, streamline supply chain logistics, and anticipate impending medical equipment maintenance requirements. Moreover, the application of predictive analytics augments clinical outcomes by sensitively detecting early signals of patient deterioration, pinpointing patients at risk of readmission, and elevating the precision of patient diagnosis and treatment.arrow_forwardAnalyzing the Amazon website explain the following: Is Amazon Content: Is the content of the selected website relevant for its intended audience? Why, why not? Is there anything they can do to make it more relevant? Social Media Integration: Is the social media component well-integrated with the website you selected? How does it work? Any recommendations? Call-for-Action: Does the website include a call-for-action component (a share, subscribe, donate, enter to win, etc.)? How does it work? How effective do you think it is? Can it be improved?arrow_forward
- Describe three ways that your organization might benefit from the use of data visualizations. Explain the content Explain intended audience Give information for each examplearrow_forwardHow is consistency exhibited in the following parts of a research paper? v Title v Theoretical Framework v Conceptual Paradigm v Statement of the Problem – Preparation of Instrumentarrow_forwardHow marketers promote value has changed dramatically since the arrival and proliferation of digital and social media. As such, ‘old school marketers’ need to retool to understand not only what roles these new media play but what relation they might have to more traditional approaches (e.g., sales, sales promotion, advertising, direct marketing…) to value promotion. Assuming the role of CMO (Chief Marketing Officer) write a departmental memo that introduces an in-service program to marketing veterans detailing what social/digital media offers the firm, the degree of fit to more traditional promotional tools, what kind of new skills/concepts they will need to learn to stay current and make a new-improved contribution to the firm’s promotional program.arrow_forward
- Why would customers have privacy concerns while making purchases on social networking sites like Facebook, which already know so much about them?arrow_forwardParaphrase this one. Analyze and elaborate in 100 words. Relying on data garnered from surveys underscores a common challenge—data accuracy. Not all respondents provide entirely truthful or precise information. Inaccuracies might stem not from dishonesty, but rather from personal biases and reservations. Consequently, inaccurate data stands to compromise the integrity of predictive insights, potentially leading businesses astray.arrow_forward1).Which of the following principles describes customer loyalty? A) customer value and satisfaction B) customer satisfaction and retention C) customer value and retention D) returning and satisfied customers NOTE: please give the answer within 2 hours thank you.arrow_forward
- Determine when information usefulness stands alone as an important criterion not addressed by the other features.arrow_forwardIn a study, causation can be best established by: A) considering a single explanation. B) evaluating the methodologies used. C) accounting for competing explanations. D) analyzing the scope of the study.arrow_forwardCritically analyse the below proposal from the Financial Conduct Authority and critically evaluate the legal principles and regulations involved in preventing similar actions of greenwashing. < "FCA proposes new rules to tackle greenwashing Press Releases First published: 25/10/2022 < In a bid to clamp down on greenwashing, the Financial Conduct Authority (FCA) is proposing a package of new measures including investment product sustainability labels and restrictions on how terms like 'ESG', 'green' or 'sustainable' can be used. < The measures are among several potential new rules which will protect consumers and improve trust in sustainable investment products. The work forms part of the commitment made in the FCA's ESG Strategy and Business Plan to build trust and integrity in ESG-labelled instruments, products and the supporting ecosystem. < There has been growth in the number of investment products marketed as 'green' or making wider sustainability claims. Exaggerated, misleading or…arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Understanding BusinessManagementISBN:9781259929434Author:William NickelsPublisher:McGraw-Hill Education
Understanding BusinessManagementISBN:9781259929434Author:William NickelsPublisher:McGraw-Hill Education Management (14th Edition)ManagementISBN:9780134527604Author:Stephen P. Robbins, Mary A. CoulterPublisher:PEARSON
Management (14th Edition)ManagementISBN:9780134527604Author:Stephen P. Robbins, Mary A. CoulterPublisher:PEARSON Spreadsheet Modeling & Decision Analysis: A Pract...ManagementISBN:9781305947412Author:Cliff RagsdalePublisher:Cengage Learning
Spreadsheet Modeling & Decision Analysis: A Pract...ManagementISBN:9781305947412Author:Cliff RagsdalePublisher:Cengage Learning Management Information Systems: Managing The Digi...ManagementISBN:9780135191798Author:Kenneth C. Laudon, Jane P. LaudonPublisher:PEARSON
Management Information Systems: Managing The Digi...ManagementISBN:9780135191798Author:Kenneth C. Laudon, Jane P. LaudonPublisher:PEARSON Business Essentials (12th Edition) (What's New in...ManagementISBN:9780134728391Author:Ronald J. Ebert, Ricky W. GriffinPublisher:PEARSON
Business Essentials (12th Edition) (What's New in...ManagementISBN:9780134728391Author:Ronald J. Ebert, Ricky W. GriffinPublisher:PEARSON Fundamentals of Management (10th Edition)ManagementISBN:9780134237473Author:Stephen P. Robbins, Mary A. Coulter, David A. De CenzoPublisher:PEARSON
Fundamentals of Management (10th Edition)ManagementISBN:9780134237473Author:Stephen P. Robbins, Mary A. Coulter, David A. De CenzoPublisher:PEARSON

Understanding Business
Management
ISBN:9781259929434
Author:William Nickels
Publisher:McGraw-Hill Education

Management (14th Edition)
Management
ISBN:9780134527604
Author:Stephen P. Robbins, Mary A. Coulter
Publisher:PEARSON

Spreadsheet Modeling & Decision Analysis: A Pract...
Management
ISBN:9781305947412
Author:Cliff Ragsdale
Publisher:Cengage Learning

Management Information Systems: Managing The Digi...
Management
ISBN:9780135191798
Author:Kenneth C. Laudon, Jane P. Laudon
Publisher:PEARSON

Business Essentials (12th Edition) (What's New in...
Management
ISBN:9780134728391
Author:Ronald J. Ebert, Ricky W. Griffin
Publisher:PEARSON

Fundamentals of Management (10th Edition)
Management
ISBN:9780134237473
Author:Stephen P. Robbins, Mary A. Coulter, David A. De Cenzo
Publisher:PEARSON