
Can some one give a detailed explanation step by step how to do this on cisco pocket tracer. thank you
Background / Scenario
Networks are constructed of three major components: hosts, switches, and routers. In this lab, you will build a simple network with two hosts and a wireless router with at least two switchports. You will apply IP addressing for this lab to the PCs to enable communication between these two devices. Use the ping utility to verify connectivity.
Required Resources
- 1 wireless router with at least two switchports
- 2 PCs running Windows with wired network cards installed
- 2 Ethernet patch cables
Instructions
Part 1: Set Up the Network Topology (Ethernet only)
In Part 1, you will cable the devices together according to the network topology.
Step 1: Power on the devices.
Power on all devices in the topology.
Step 2: Connect the PCs to the switch.
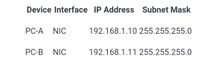
a. Connect one end of an Ethernet cable to the NIC port on PC-A. Connect the other end of the cable to a switchport on the wireless router. After connecting the PC to the switchport, you should see the light for the switchport turn amber Bnd then green, indicating that PC-A has been connected correctly.
b. Repeat the same procedure for PC-B
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

- How important is network security to an enterprise in this globalized world? What are some of the issues with the current networks acting as Wide Area Networks (WANs)?arrow_forwardThe AIS's many network types, each with its own set of benefits and drawbacksarrow_forwardCompare system development and system maintenance costs for e-commerce. Which is more expensive and why?arrow_forward
- Discuss the strategies and technologies used in Mobile Device Management (MDM) to ensure data privacy and compliance with regulations like HIPAA and GDPR in healthcare and finance sectors.arrow_forwardAnalyze the challenges and solutions related to mobile device assistance in highly regulated industries such as healthcare and finance.arrow_forwardThe AB e-commerce company has started operating by using a 3PL partner and benefits from saving time and money with a more streamlined order fulfillment process and inventory management. By outsourcing fulfillment, the 3PL is automatically notified when an order is placed.Also, partnering with a 3PL helps reduce logistics costs in the long run. Unlike hiring an internal team to manage inventory and shipping, 3PLs store the inventory and their team of fulfillment experts are trained to keep overall logistics costs down. Furthermore, 3PL arrangement helps split inventory across locations so the company can eliminate shipping to the highest, most expensive shipping zones and keep inventory closer to more customers.To have a more integrated distribution process, would reducing dependency on 3PL be a viable option in the long term for the AB company for cost management and control? Justify with your understanding of supply chain management concepts. also, using your knowledge of other open…arrow_forward
- Networks would be inoperable without protocols. Explain their importance and what functions they perform.arrow_forwardShould organizations use software service providers which include cloud services for all their software needs? Discuss why or why not? Further discuss the factors relating to people, organization, and technology that need to be considered when making the above decision.arrow_forwardIT Service Management strategies are critical for ensuring users and management get the desired level of service. Describe the primary IT service delivery pillars and their influence on enterprises.arrow_forward
 Practical Management ScienceOperations ManagementISBN:9781337406659Author:WINSTON, Wayne L.Publisher:Cengage,
Practical Management ScienceOperations ManagementISBN:9781337406659Author:WINSTON, Wayne L.Publisher:Cengage, Operations ManagementOperations ManagementISBN:9781259667473Author:William J StevensonPublisher:McGraw-Hill Education
Operations ManagementOperations ManagementISBN:9781259667473Author:William J StevensonPublisher:McGraw-Hill Education Operations and Supply Chain Management (Mcgraw-hi...Operations ManagementISBN:9781259666100Author:F. Robert Jacobs, Richard B ChasePublisher:McGraw-Hill Education
Operations and Supply Chain Management (Mcgraw-hi...Operations ManagementISBN:9781259666100Author:F. Robert Jacobs, Richard B ChasePublisher:McGraw-Hill Education
 Purchasing and Supply Chain ManagementOperations ManagementISBN:9781285869681Author:Robert M. Monczka, Robert B. Handfield, Larry C. Giunipero, James L. PattersonPublisher:Cengage Learning
Purchasing and Supply Chain ManagementOperations ManagementISBN:9781285869681Author:Robert M. Monczka, Robert B. Handfield, Larry C. Giunipero, James L. PattersonPublisher:Cengage Learning Production and Operations Analysis, Seventh Editi...Operations ManagementISBN:9781478623069Author:Steven Nahmias, Tava Lennon OlsenPublisher:Waveland Press, Inc.
Production and Operations Analysis, Seventh Editi...Operations ManagementISBN:9781478623069Author:Steven Nahmias, Tava Lennon OlsenPublisher:Waveland Press, Inc.





