
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
Ccfgggg
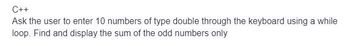
Transcribed Image Text:C++
Ask the user to enter 10 numbers of type double through the keyboard using a while
loop. Find and display the sum of the odd numbers only
SAVE
AI-Generated Solution
info
AI-generated content may present inaccurate or offensive content that does not represent bartleby’s views.
Unlock instant AI solutions
Tap the button
to generate a solution
to generate a solution
Click the button to generate
a solution
a solution
Knowledge Booster
Similar questions
- Cryptography: Using the Euclidean Algorithm find the greatest common divisor (gcd) of the following: a) 155 37 b) 1114978 23456 c) 110010105 750arrow_forwardThe Internet has evolved into a crucial medium for exercising one's right to freedom of expression. Facebook and Twitter are both being used by a large number of individuals and organizations to disseminate hate speech. Should there be no limits placed on what people may say online? Where should the line be drawn when it comes to limiting hate speech on social media?arrow_forwardThe Internet has become an increasingly important medium via which individuals may exercise their right to free speech. Facebook and Twitter are being used by a lot of different people and organisations to spread anti-Semitic information. Is free expression on the internet a right or a privilege? How far should social media companies go to stop the spread of information that promotes hatred?arrow_forward
- What are some of the possible outcomes for a person who gets spoofed?arrow_forwardHence, the Internet has become an essential tool for exercising one's right to free expression. Several individuals and groups are guilty of misusing social media sites like Facebook and Twitter to propagate hate speech. Should there be any limits placed on how individuals may share their ideas online? Where should the line be set when it comes to allowing nasty remarks on social networking sites?arrow_forwardIn today’s technologically advanced society, is there really privacy? Based on your own personal experiences with social media (Facebook, Twitter, Tik Tok, Instagram, or Snapchat), do you feel that individuals should be held accountable for their actions outside of the workplace? Is it possible that, due to the technological advances in smart phones, tablets, and other communication devices, workplace and personal privacy have meshed together to a point that what was once personal space is now fair game in the hiring and firing practices?arrow_forward
- Are there any advantages to accessing the internet for persons who have mental or physical limitations? In what ways do you think persons who have impairments may benefit from emerging technologies? To what extent does making assistive technology open-source have positive and negative effects?arrow_forwardCS 386 Project: Overview Project Synopsis: This group project will require your group to design and implement your own enciphering algorithm. Your team's algorithm must combine the two operations, substitution and permutation/transposition, into your unique encryption algorithm. Your encryption algorithm must include multiple rounds of the two operations. You program must be able to encrypt and decrypt messages. Your team will need to give your algorithm a name that is unique to your encryption technique. Your group mayarrow_forwardNeed only the correct answerarrow_forward
- How are ElGamal Signatures produced and validated?arrow_forwardQuestion 9 Full explain this question and text typing work only thanksarrow_forwardDo you believe that it is feasible to build a bogus digital signature that is based on the RSA algorithm? Please explain why you either agree or disagree with the statement, regardless of which camp you fall into.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education