Question
Given a table of the eight different types of analysis, similar to the attached table. an then selected three recent attacks , and for each attack, explain if you think it could have been prevented by each of the data correlations.
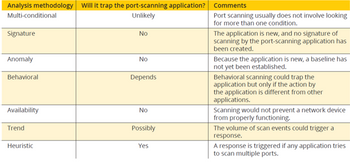
Transcribed Image Text:Analysis methodology Will it trap the port-scanning application? Comments
Multi-conditional
Signature
Anomaly
Behavioral
Unlikely
No
No
Depends
Availability
No
Trend
Possibly
Heuristic
Yes
Port scanning usually does not involve looking
for more than one condition.
The application is new, and no signature of
scanning by the port-scanning application has
been created.
Because the application is new, a baseline has
not yet been established.
Behavioral scanning could trap the
application but only if the action by
the application is different from other
applications.
Scanning would not prevent a network device
from properly functioning.
The volume of scan events could trigger a
response.
A response is triggered if any application tries
to scan multiple ports.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 1 steps

Knowledge Booster
Similar questions
- Outline the procedure followed in a downgrade attack.arrow_forwardWhen you say "header-based vulnerabilities," what exactly do you mean? Name three examples that spring to mind.arrow_forwardFor the benefit of those who do not know, what exactly is a "poison package assault?" There need to be at least two instances provided for this assault, right?arrow_forward
- When you say "header-based vulnerabilities," what do you mean? Who can name three such things?arrow_forwardWhat do you mean exactly when you say "the objectives of authentication"? Think about the benefits and drawbacks of each system, then make your decision on these comparisons.arrow_forwardWhen you say "header-based vulnerabilities," what exactly do you mean? Name three examples that spring to mind.arrow_forward
- What precisely is meant by the term "Trojan horse," and how does its implementation take place in real life? There need to be a total of three examples provided.arrow_forwardWhat does it mean when someone launches a "poison package assault," and how would one carry one out? Kindly include two instances of such attack, if possible.arrow_forwardIf I may ask, what exactly are "header-based vulnerabilities"? Name three examples that spring to mind.arrow_forward
- "Header-based vulnerabilities"—what does that mean?Could you provide three examples?arrow_forwardGive some instances of information that is not covered by the Security Rule.arrow_forwardWhen you say "header-based vulnerabilities," what exactly do you mean? Name three examples that spring to mind.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios