
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
thumb_up100%
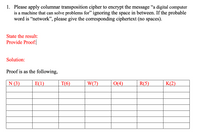
Transcribed Image Text:1. Please apply columnar transposition cipher to encrypt the message "a digital computer
is a machine that can solve problems for" ignoring the space in between. If the probable
word is "network", please give the corresponding ciphertext (no spaces).
State the result:
Provide Proof:
Solution:
Proof is as the following,
N (3)
E(1)
T(6)
W(7)
O(4)
R(5)
K(2)
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- A.Given p=25, q=9, and e=7, generate the public key (n,e) and the private key (n,d) using the RSA Key generation algorithm. (Use Excel for computations) b. Given Bob's public key of (85, 7) and private key of (85, 55), show how Alice can encrypt m=3 to send to Bob. Show the ciphertext. c. Given Bob's public key of (85, 7) and private key of (85, 55), show how Bob can decrypt the ciphertext y=2 received from Alice. Show the plaintext. d. Using the fast exponentiation method, determine 530 mod 47. Show your work.arrow_forwardWhat will be the ciphered text corresponding to “ALGORITHM” if bifid cipher is used for encryption with key as “KEY” with a period as 5? a) SBPISZTKZH b) PLNSOWGKQM c) SELFQEXBHM d) YFSGWNFBWarrow_forwardMany forms of cryptography are based on the following discrete log problem. Choose a cyclic group G (produced by one generator g) with finitely many elements. Alice and Bob want to set up a secret communication and need a secret key for that, which becomes a group element from G. They set up the following exchange (the so-called Diffie-Hellman protocol): 1. Alice chooses a secret group element a and sends unsecured g^a to Bob 2.Bob chooses a secret group element b and sends unsecured g^b to Alice 3. Alice calculates (g^b )^a and keeps this group element secret 4.Bob calculates (g^a )^b and keeps this group element secret Since a cyclic group is abelian, Alice and Bob now share the secret key (g^b )^a=(g^a )^b. The blue group elements are publicly known, the red elements are secret. The discrete log problem presented to an eavesdropper is computing say a from the publicly known data G,g,g^a. The naming of the problem comes from the solution a= glog(ga ) which is generally difficult to…arrow_forward
- . Consider the alphabet Σ = {0,1}. Give regular expressions generating the following lan- guages. (a) {w ¤ Σ* | w begins with a 0 and ends with a 1} (b) {w € Σ* | w contains at least four Os} 1* (c) {w € Σ* | w contains the substring 1101} (d) {w € Σ* | w has length at least 4 and its third symbol is a 0} (e) {w € Σ* | w begins with a 0 and has even length, or begins with a 1 and has odd length} (f) {€,0} (g) The empty set (h) All strings over Σ (i) All strings over Σ except the empty stringarrow_forwardConsider a very simple symmetric block encryption algorithm in which 32-bits blocks of plaintext are encrypted using a 64-bit key. Encryption is defined as C = (PK₁) K₁ where C = ciphertext, K = secret key, Ko = leftmost 64 bits of K, K₁ = rightmost 64 bits of K,+ = bitwise exclusive OR, and is addition mod 264. a. Show the decryption equation. That is, show the equation for P as a function of C, Ko, and K₁. b. Suppose and adversary has access to two sets of plaintexts and their correspond- ing ciphertexts and wishes to determine K. We have the two equations: C = (PK) K₁; C = (PK) K₁ First, derive an equation in one unknown (e.g., Ko). Is it possible to proceed fur- ther to solve for Ko?arrow_forwardA.Given p=25, q=9, and e=7, generate the public key (n,e) and the private key (n,d) using the RSA Key generation algorithm. (Use Excel for computations) b. Given Bob's public key of (85, 7) and private key of (85, 55), show how Alice can encrypt m=3 to send to Bob. Show the ciphertext. c. Given Bob's public key of (85, 7) and private key of (85, 55), show how Bob can decrypt the ciphertext y=2 received from Alice. Show the plaintext. d. Using the fast exponentiation method, determine 530 mod 47. Show your work.arrow_forward
- Describe the differences between a monoalphabetic cipher and a polyalphabetic cipher. Is the Caesar cipher a polyalphabetic cipher? In one of his cases, Sherlock Holmes was confronted with the following message: Znk yozagzout oy mxgbk. Iusk osskjogzkre Although Watson was puzzled, Holmes was immediately able to deduce the type of cipher. Describe the cipher being used to encrypt this message. Can you decode the message? Is this cipher susceptible to brute-force cryptanalysis?arrow_forward2.(a) Consider the use of OTP. Let m be an arbitrary message to be encrypted and c be a given ciphertext in the ciphertext space. How many possible keys with which m can be mapped to c, i.e., f(m,k)=c? None 1 2 The size of the key space Depends on m (b) 3^(-n) is negligible. True or false? (c) n^(-100) is negligible. True or false?arrow_forwardPlease show explaintion for steps and the formulas used thank you.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education