
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
Can someone answer these 3 questions?
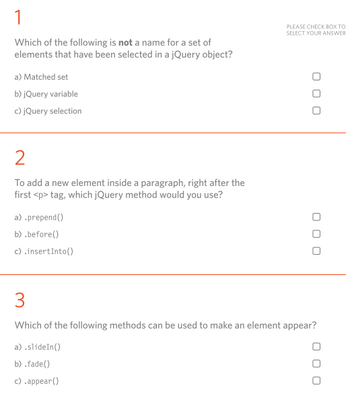
Transcribed Image Text:1
Which of the following is not a name for a set of
elements that have been selected in a jQuery object?
a) Matched set
b) jQuery variable
c) jQuery selection
2
To add a new element inside a paragraph, right after the
first <p> tag, which jQuery method would you use?
a) .prepend()
b) .before()
c).insertInto()
PLEASE CHECK BOX TO
SELECT YOUR ANSWER
000
000
3
Which of the following methods can be used to make an element appear?
a) .slideIn()
b).fade()
c) .appear()
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 5 steps

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Where do limits on access fit into modern culture? Please include at least two instances of such restrictions in your response.arrow_forwardPlease follow the steps precisely I have asked for help on this question repeatedly and it seems like people keep giving me incomplete answers I have talked talk to your support team and they told me to just resubmit it it may be due to that particular expert not fully understanding the material So I'm just going to keep uploading this because it is what your support team there at Bartleby told me to do they also told me to start giving thumbs down on the ones that were wrong or incomplete so that is what I'm going to doarrow_forwardIn this essay, we will analyze the two fingerprinting methods that are the most used.arrow_forward
- Are you certain that employing wireless applications for mistake correction is more effective? You should provide evidence to back up your claims with.arrow_forwardHow does secret key cryptography function? Please provide a short explanation, maybe with an illustration of how the system used to work. What recent experiences do you have with it?arrow_forwardGive an in-depth comparison and contrast of any two modes of communication and your reasoning for choosing one over the other. Give reasons to back up your response.arrow_forward
- Answer each as shortly yet concisely as possible....... 1. Use examples to show what is false negative and what is false positive. 2. Password is the most common authentication method. Is it strong authentication? Discuss the pros and cons of password authentication.3. Give at least three examples of authentication used in your school, workplace, or daily life. Which authentication category does each of them belong to? 4. How are authentication and authorization alike and how are they different. What is the relationship between the two? Please explain using example(s). 5. Use example(s) to explain one of the access control models (MAC, DAC, RBAC, Rule-based AC, and ABAC). 6. Discuss the difference between a Telnet and a SSH. 7. Give two examples on where Kerberos authentication is used. 8. Discussion the differences between Windows file permissions and UNIX/Linux file permissions. 9. Discuss the pros and cons of fingerprint authentication. 10. Use example(s) to show why multi-factor…arrow_forwardHow would I answer this problem please show steps? F6arrow_forwardHow does secret key cryptography function? Please provide a short explanation, maybe with an illustration of how the system used to work. What recent experiences do you have with it?arrow_forward
- In what many forms may information be exchanged? Could you give me an example of what you mean?arrow_forward4) Question 2 asked you to compute the number of possible passwords with various numbers of characters. However, it seems more likely that most people will choose actual words for their password. According to the website wordfinder.yourdictionary.com, the English language has approximately 23,000 six-letter words. a) Assume that a password must be at least 8 characters long and include at least 1 digit and at least 1 special character (again, assume there are 30 of these that are allowed). If people form their password by taking an English word of exactly 6 letters (assume that this password is not case-sensitive) and then adding (in either order) a digit and a special character (e.g flames#1), how many passwords would be possible? (Hint: Find the number of passwords with 6 letters followed by a digit and a special character, then exchange the order of the last two characters.) b) How does your answer change if we assume passwords are case-sensitive and the password must…arrow_forwardWhy do we have to verify our identities if nobody believes us? Compare and contrast the different methods of verification currently in use?arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education