Related questions
Question
Apply Warshall’s algorithm to find the transitive closure of the digraph defined by the following adjacency matrix:
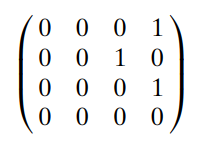
Transcribed Image Text:0001
0 0 1 0
0001
000
00
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps
