Many services like, for example email and chats, are now being
done over hbp and hbps protocols. Now network security admins have a
problem in the sense that these services are increasingly encrypted with
sophis8cated technologies, and the ability to process packets goes down.
Let us assume that you are one such admin. Your company (rightly so) does
not want you to write programs execu8ng on employee computers to
monitor what employees send and receive over the Internet due to privacy
expectations. Things like capturing user screens, key stroke loggers are not
allowed. What you can monitor though is router/ firewall traffic, since that
is off limits to employees. In this case, do you completely give up logging
packets at router side due to encryption, or is there some use to logging IP
packets at the router for security purposes? Please justify keeping common
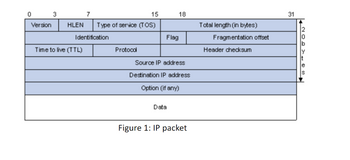
abacks we saw in class in mind. Recall how a packet at the router looks like
below. Payload is the actual data portion (most likely encrypted).
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps
