Question
thumb_up100%
Hello. Please answer the attached Computer Algorithms question correctly.
*If you answer the question correctly, I will give you a thumbs up. Thanks.
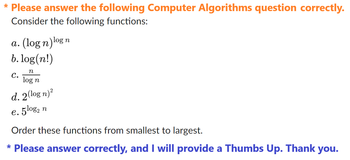
Transcribed Image Text:* Please answer the following Computer Algorithms question correctly.
Consider the following functions:
a. (log n)log
b.log(n!)
n
C.
log n
d. 2(log n)²
5 log₂ n
e.
n
Order these functions from smallest to largest.
* Please answer correctly, and I will provide a Thumbs Up. Thank you.
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 3 steps with 11 images

Knowledge Booster
Similar questions
- EXPALIN DEEPLY!!!! (Aglie model) WRITE A PARAGRAPH NO COPY PASTE WRITE YOUR OWN WORD NO HANDWRITING, THANK YOU!arrow_forwardPlease explain what jQuery-UI widget is in Interactive Web Applications. Please give a coding example. Thanksarrow_forwardQ : Give a detail description of genetic algorithm used in various field.arrow_forward
arrow_back_ios
arrow_forward_ios